Load Time and Network Security: Ensuring Fast and Secure Web Performance
Load Time and Network Security: Ensuring Fast and Secure Web Performance
Chapter 1: Introduction to Load Time and Network Security
Understanding the importance of load time and network security in web performance
In today’s digital age, where the internet is an integral part of our lives, it is crucial to comprehend the significance of load time and network security in web performance. This subchapter aims to shed light on the factors that affect website load time on different devices and browsers, emphasizing the need for a secure and fast online experience.
Load time refers to the time it takes for a webpage to be fully displayed on a user’s screen. It plays a pivotal role in determining user satisfaction and engagement. Research has shown that users tend to abandon websites that take longer than a few seconds to load. This can have a detrimental impact on businesses, leading to lost revenue and a decline in customer trust. Therefore, understanding the factors that affect load time is essential for optimizing web performance.
One such factor is the device being used to access the website. Different devices have varying processing power and internet connectivity, which directly influence load time. Additionally, the browser being used can also impact load time. Compatibility issues between certain browsers and website elements can lead to longer load times, making it crucial for web developers to ensure compatibility across multiple browsers.
However, load time is not the sole concern when it comes to web performance. Network security is equally paramount in safeguarding sensitive information and maintaining user trust. Cybersecurity threats are increasingly prevalent, with cybercriminals constantly devising new techniques to exploit vulnerabilities. Email, social security numbers, bank accounts, and other personal information are at risk of being compromised if proper network security measures are not in place.
Firewalls, scanning and monitoring systems, and secure passwords are some of the fundamental tools utilized to protect against network security attacks. Website security is also crucial in preventing unauthorized access and ensuring the integrity and confidentiality of user data.
To summarize, load time and network security are two critical aspects of web performance that need to be understood and addressed to provide users with a fast and secure online experience. By optimizing load time on different devices and browsers and implementing robust network security measures, businesses and individuals can protect sensitive information, maintain user trust, and enhance overall web performance.
Chapter 2: Factors Affecting Website Load Time

Device-specific factors influencing website load time
Device-specific factors play a significant role in determining the load time of a website. With the increasing variety of devices and browsers available today, it is crucial for website developers and administrators to understand these factors in order to optimize the website’s performance. This subchapter explores the various device-specific factors that can influence website load time, and provides insights on how to address these issues for a fast and secure web performance.
One of the key factors that affect website load time on different devices is the hardware capability. Different devices have varying processing power, memory, and storage capacities. Websites that are heavy in terms of multimedia content, such as images and videos, may take longer to load on devices with lower hardware capabilities. It is essential to optimize the website’s content and design to ensure compatibility across a wide range of devices.
Another factor to consider is the operating system and browser being used on the device. Different operating systems may have different rendering engines, which can affect how the website is displayed and loaded. Similarly, different browsers have their own rendering engines and may interpret website code differently. It is important to test the website on various browsers and operating systems to ensure consistent and optimized performance.
Network connectivity is also a crucial factor in website load time. Devices may have different network capabilities, such as 3G, 4G, or Wi-Fi. The website should be optimized to load quickly on slower network connections, while still providing an optimal experience for users with faster connections. This can be achieved through techniques like lazy loading, caching, and minimizing the use of external resources.
Furthermore, security measures such as firewalls and network protection attacks can also impact website load time. While these measures are essential for safeguarding sensitive data like emails, social security numbers, and bank accounts, they can introduce additional latency. Website administrators should strike a balance between security and performance by implementing efficient security protocols and minimizing unnecessary network requests.
In conclusion, understanding device-specific factors is crucial for ensuring fast and secure web performance. Factors such as hardware capability, operating system and browser compatibility, network connectivity, and security measures all play a role in website load time. By optimizing the website’s content, design, and code, developers can deliver a seamless experience across different devices and browsers while maintaining the necessary security measures for safeguarding sensitive data.
Impact of hardware specifications on load time
In today’s fast-paced digital world, where users expect websites to load within seconds, the hardware specifications of a device play a significant role in determining the load time of a website. Whether it’s a desktop computer, laptop, tablet, or smartphone, the hardware capabilities directly impact the user experience and overall website performance. This subchapter explores the influence of hardware specifications on load time and how it affects cybersecurity.
One of the primary factors affecting website load time on different devices and browsers is the device’s processing power. Devices with higher processing power can handle complex tasks and render web pages quickly. On the other hand, older or low-end devices may struggle to process heavy websites, resulting in slower load times. Cybersecurity professionals must consider this aspect as slower load times can increase the risk of users leaving a website before it fully loads, potentially exposing sensitive data such as emails, social security numbers, and bank accounts.
Another hardware specification that impacts load time is the amount of RAM (random access memory) available on a device. RAM plays a crucial role in storing and accessing data quickly. Websites with rich media content, such as high-resolution images and videos, require more RAM to load efficiently. Insufficient RAM can lead to slower load times, affecting user experience and potentially leaving the website vulnerable to network protection attacks.
Additionally, the type of storage device also influences load time. Solid-state drives (SSDs) are significantly faster than traditional hard disk drives (HDDs) because they have no moving parts and offer faster data access. Websites hosted on servers with SSDs can load quicker than those on servers with HDDs. Cybersecurity professionals must ensure that the websites they manage are hosted on servers with SSDs to provide faster load times and better network security.
Moreover, the network connection speed of a device is essential for load time. Devices connected to high-speed internet connections will load websites faster than those on slower connections. Cybersecurity professionals must consider this factor when analyzing website load times and network security. Slower load times can increase the risk of security vulnerabilities and potential attacks.
In conclusion, hardware specifications play a crucial role in determining website load time and its impact on cybersecurity. Factors such as processing power, RAM, storage type, and network connection speed directly influence how quickly a website loads on different devices and browsers. Cybersecurity professionals must understand these hardware-related factors to optimize load times, enhance website security, and protect sensitive information from potential threats.
Effect of software configurations on load time
In today’s digital world, where online security is a paramount concern, load time plays a crucial role in the overall user experience. Slow loading websites not only frustrate users but also pose potential security risks. This subchapter aims to discuss the effect of software configurations on load time, specifically addressing the factors that affect website load time on different devices and browsers.
When it comes to website load time, several factors come into play. One significant factor is the software configuration employed by the website. The software configurations, including server settings, caching mechanisms, and content delivery networks (CDNs), can significantly impact the website’s load time.
Firstly, server settings play a vital role in determining load time. Optimizing server configurations, such as enabling compression, reducing server response time, and leveraging browser caching, can dramatically improve load speed. By compressing files and reducing response time, the server can efficiently deliver web content to the user’s device, resulting in faster load times.
Secondly, caching mechanisms significantly affect load time. By implementing browser caching and server-side caching, websites can store frequently accessed content, reducing the need for repetitive content retrieval. When a user revisits the website, cached content can be retrieved locally, resulting in faster load times. Additionally, CDNs can distribute website content across multiple servers globally, reducing the distance between the user and the server, further enhancing load time.
Moreover, the choice of browsers and devices can impact load time. Different browsers interpret website code differently, and certain configurations may not be compatible with all browsers. Web developers must ensure compatibility across major browsers to ensure consistent and fast load times. Additionally, the device being used to access the website plays a role in load time. Mobile devices, for instance, may have slower processing power or limited network connectivity, necessitating optimized software configurations to ensure optimal load times.
In conclusion, software configurations play a pivotal role in determining website load time. Optimized server settings, caching mechanisms, and compatibility with different browsers and devices are crucial factors to consider. By implementing these configurations, websites can ensure fast load times, enhancing user experience while maintaining network security. It is essential for cybersecurity professionals, web developers, and anyone involved in website management to understand the effect of software configurations on load time to guarantee fast and secure web performance.
Browser-specific factors affecting website load time
Browser-specific factors can have a significant impact on the load time of a website. When it comes to optimizing website performance, it is crucial to understand how different browsers handle and render web content. This subchapter will delve into the various browser-specific factors that affect website load time, providing valuable insights for cybersecurity professionals and anyone concerned about network security.
One of the key factors influencing website load time is browser caching. Caching allows browsers to store certain elements of a website, such as images and scripts, locally on the user’s device. This enables faster loading of subsequent pages as the cached content does not need to be fetched from the server again. However, different browsers have different caching mechanisms, and understanding these differences can help optimize website performance across multiple platforms.
Browser rendering engines also play a crucial role in website load time. Each browser utilizes its own rendering engine, which determines how the HTML, CSS, and JavaScript code is interpreted and displayed to the user. For example, Google Chrome uses the Blink rendering engine, while Firefox uses Gecko. These engines have their own strengths and weaknesses, and understanding their nuances can help developers optimize a website’s code for faster rendering across different browsers.
Another important factor to consider is the support for various web technologies and standards. Browsers differ in their level of compliance with web standards, such as HTML5, CSS3, and JavaScript APIs. This can result in variations in how a website is displayed and executed across different browsers. By understanding these differences, developers can ensure that their websites are compatible with a wide range of browsers, reducing load time discrepancies.
Additionally, browser add-ons and extensions can impact website load time. Some extensions, such as ad blockers and security plugins, may introduce additional processing time and affect the overall performance of a website. It is important to be aware of these potential bottlenecks and optimize the website accordingly.
In conclusion, browser-specific factors have a significant impact on website load time. By considering caching mechanisms, rendering engines, web standards compliance, and the impact of browser add-ons, developers and cybersecurity professionals can optimize websites for faster and more consistent performance across different devices and browsers. This knowledge is crucial for ensuring a secure and fast web experience for users while protecting sensitive information such as emails, social security numbers, and bank accounts.
Compatibility issues and their impact on load time
Compatibility issues can have a significant impact on the load time of a website, affecting both user experience and overall performance. In today’s digital landscape, where cybersecurity and network security are of utmost importance, understanding these compatibility issues becomes crucial to ensure fast and secure web performance.
One of the primary factors affecting website load time on different devices and browsers is the diversity of operating systems and web browsers available in the market. Each device and browser may interpret and render web content differently, leading to compatibility issues. For example, a website that functions flawlessly on one browser may experience layout issues or broken functionality on another.
Incompatibility can arise due to variations in HTML, CSS, and JavaScript rendering across different browsers. This means that website developers need to ensure their code is optimized and compatible with various browsers and versions. Failure to do so can result in slower load times and a poor user experience.
Another factor influencing load time is the lack of support for certain web technologies or plugins on specific devices or browsers. For instance, some older browsers may not support modern web technologies like HTML5 or CSS3, resulting in degraded performance or broken functionality. Similarly, some mobile devices may not support certain plugins or scripts, leading to slower load times or even inaccessibility of website features.
Compatibility issues can also stem from differences in network capabilities across devices and browsers. For example, mobile devices may have slower internet connections compared to desktop computers. Websites that are not optimized for lower bandwidths can take longer to load, leading to user frustration and potentially higher bounce rates.
To address these compatibility issues and ensure fast and secure web performance, it is important to adopt a comprehensive approach. This includes regularly testing websites on different devices and browsers, optimizing code for compatibility, and leveraging responsive web design techniques to ensure a consistent experience across devices.
Furthermore, implementing firewall and network protection measures can help safeguard against potential attacks while maintaining website performance. Scanning and monitoring for vulnerabilities, securing passwords, and implementing robust website security protocols are also essential to protect sensitive user information such as social security numbers and bank accounts.
In conclusion, compatibility issues can significantly impact website load time, affecting user experience and overall performance. Understanding the factors that contribute to these issues and implementing appropriate measures to address them is crucial for ensuring fast and secure web performance in today’s cybersecurity-focused environment.
Browser caching and its role in load time optimization
Browser caching is an essential technique in optimizing load time for websites across different devices and browsers. In this subchapter, we will explore the role of browser caching in load time optimization and how it affects the security of your website.
When a user visits a website, their browser downloads all the necessary files, including HTML, CSS, JavaScript, and images, to display the web page. This process takes time and contributes to the overall load time of the website. However, with browser caching, this process can be significantly improved.
Browser caching allows a website to store certain files locally on a user’s device. When the user revisits the same website, instead of redownloading all the files, the browser retrieves them from the local cache. This results in a much faster load time as the browser doesn’t need to make multiple requests to the server.
The benefits of browser caching are twofold. Firstly, it reduces the load on the website’s server, as the server doesn’t have to handle repeated requests for the same files. This can lead to improved server performance and scalability. Secondly, it improves the user experience by delivering faster load times, which in turn can increase user engagement and retention.
However, while browser caching offers significant advantages, it also raises security concerns. Cached files can potentially be accessed by unauthorized individuals, especially if sensitive information like emails, social security numbers, or bank accounts are stored in them. Therefore, it is crucial to implement proper security measures to safeguard against any potential threats.
One way to address this issue is by setting appropriate cache control headers on the server-side. These headers instruct the browser on how to cache and handle the files. By implementing proper cache control policies, you can control the caching behavior of different files and ensure that sensitive data is not stored in the cache.
Additionally, it is essential to regularly monitor and scan your website for any vulnerabilities or security threats. Employing a robust scanning and monitoring system can help identify any potential risks and take appropriate actions to mitigate them. Furthermore, enforcing strong and secure passwords, implementing a firewall, and staying updated with the latest security patches are crucial steps in maintaining the security of your website.
In conclusion, browser caching plays a crucial role in load time optimization for websites across different devices and browsers. It significantly improves load times, reduces server load, and enhances user experience. However, it is important to implement proper security measures to protect sensitive data and ensure the overall safety and security of your website. By following best practices in website security and staying vigilant against potential threats, you can optimize load times while maintaining the highest level of network security.
Chapter 3: Enhancing Load Time on Different Devices and Browsers

Optimizing website design and coding for mobile devices
In today’s digital age, mobile devices have become the primary means for accessing the internet and consuming online content. As a result, it is crucial for businesses and website owners to optimize their website design and coding specifically for mobile devices. This subchapter aims to discuss the factors that affect website load time on different devices and browsers, and how to address them to ensure a fast and secure web performance.
When it comes to website load time, there are several factors that can impact the user experience on different devices and browsers. One key factor is the device’s processing power and internet connection. Mobile devices, especially older models, may have limited processing capabilities and slower internet connections, which can significantly affect website load time. Additionally, different browsers have their own rendering engines and may handle website code differently, leading to variations in load time.
To optimize website design and coding for mobile devices, it is crucial to take these factors into consideration. One effective approach is to implement responsive web design, which allows the website to adapt and adjust its layout based on the user’s device and screen size. This ensures that the content is displayed correctly and optimally on any device, improving the overall user experience.
Another important aspect is to optimize the website’s code and minimize unnecessary elements that can slow down the load time. This includes compressing images, reducing the number of HTTP requests, and minifying CSS and JavaScript files. By doing so, the website’s file sizes are reduced, resulting in faster load times on mobile devices.
Furthermore, implementing caching mechanisms can significantly improve website load time. Caching allows the browser to store certain website elements locally, reducing the need to fetch them from the server every time the user visits the website. This can greatly enhance the performance and speed of the website, especially on mobile devices with limited processing power.
In terms of browser compatibility, it is essential to test and optimize the website for different browsers and versions. This ensures that the website functions and loads properly across a wide range of devices and browsers, providing a consistent user experience for all users.
In conclusion, optimizing website design and coding for mobile devices is crucial in today’s digital landscape. By considering factors such as device processing power, internet connection, and browser compatibility, businesses can ensure a fast and seamless user experience. Implementing responsive design, minimizing file sizes, and utilizing caching mechanisms are some effective strategies to optimize website load time on different devices and browsers. By prioritizing these optimization techniques, businesses can provide a secure and efficient online experience for their users.
Responsive design and its impact on load time
Responsive design refers to the approach of designing and developing websites that can adapt and respond to different screen sizes and devices. In today’s digital age, where users access websites from various devices such as desktops, laptops, tablets, and smartphones, responsive design has become essential for delivering a seamless user experience. However, it is important to understand the impact of responsive design on load time and how it can affect website performance.
Load time is a critical factor that can greatly impact user experience and ultimately determine the success or failure of a website. Slow loading websites not only frustrate users but also have a direct impact on conversion rates and search engine rankings. With users becoming increasingly impatient, it is imperative for websites to load quickly across all devices and browsers.
Responsive design can have both positive and negative effects on load time. On the positive side, a responsive design eliminates the need for separate mobile and desktop versions of a website, reducing maintenance efforts and ensuring consistent content across all devices. This can potentially lead to faster load times as the website’s code and assets are optimized for a unified experience.
However, responsive design can also introduce challenges that impact load time. One of the main factors affecting load time on different devices and browsers is the size of the website’s assets, including images, videos, and scripts. When a responsive website loads on a mobile device, the assets may still be designed for larger screens, resulting in unnecessary data being transferred and slower load times. Optimizing and compressing assets for different devices and browsers can help mitigate this issue.
Another factor to consider is the layout and structure of a responsive website. The complexity of responsive layouts can increase the amount of code that needs to be processed by the browser, leading to slower load times. It is crucial to strike a balance between design aesthetics and performance optimization to ensure fast load times across devices.
In conclusion, responsive design is crucial for delivering a seamless user experience across devices. However, it is important to be mindful of the impact it can have on load time. By optimizing assets, streamlining code, and finding the right balance between design and performance, websites can ensure fast load times and enhance user satisfaction.
Mobile-specific optimization techniques for faster load time
In today’s digital era, where people rely heavily on their mobile devices for browsing the internet, it is crucial for website owners to ensure fast and seamless user experiences across different devices and browsers. Slow load times can have a significant impact on user engagement and can even lead to potential security risks. This subchapter explores mobile-specific optimization techniques that can help enhance website load time on various devices and browsers.
Factors affecting website load time on different devices and browsers
Before diving into the optimization techniques, it is essential to understand the factors that can affect website load time on different devices and browsers. The screen size, processing power, and network speed of mobile devices vary significantly compared to desktop computers. Additionally, different browsers have different rendering engines, which can affect how a website is displayed and loaded.
Optimization techniques for mobile devices
- Responsive design: Implementing responsive design ensures that the website adapts and adjusts its layout based on the screen size and orientation of the device. This helps eliminate the need for separate mobile-specific websites and improves load time.
- Image optimization: Mobile devices often have slower network speeds and limited bandwidth. Optimizing images by compressing them and using appropriate file formats can significantly reduce load times without compromising image quality.
- Minify CSS, JavaScript, and HTML: Removing unnecessary white spaces, comments, and reducing file sizes of CSS, JavaScript, and HTML files can help improve load time on mobile devices.
- Caching: Utilizing browser caching allows for storing static resources, such as CSS and JavaScript files, locally on the device. This reduces the need for repeated downloads and speeds up subsequent visits to the website.
- Lazy loading: Implementing lazy loading techniques helps defer the loading of non-critical resources, such as images and videos, until they are needed. This approach can significantly improve initial load times.
Optimization techniques for different browsers
- Browser-specific optimizations: Different browsers have their quirks and performance characteristics. It is essential to identify and address any browser-specific issues to ensure optimal load times across various browsers.
- Code optimization: Reviewing and optimizing code, such as eliminating unnecessary scripts or reducing the use of external resources, can improve load time on different browsers.
- Browser caching: Leveraging browser caching techniques can help reduce the number of requests made to the server, resulting in faster load times.
By implementing these mobile-specific optimization techniques, website owners can ensure faster load times on different devices and browsers. Not only does this enhance user experiences, but it also reduces the risk of users abandoning the website due to slow load times. Additionally, faster load times contribute to improved network security by reducing the window of vulnerability for potential attacks. In the fast-paced digital landscape, where speed and security are paramount, optimizing websites for mobile devices and different browsers is crucial for success.
Browser-specific load time optimization strategies
Browser-specific load time optimization strategies are essential for ensuring fast and secure web performance. In today’s digital landscape, where cybersecurity threats are rampant, it is crucial to prioritize the speed and security of websites, especially when dealing with sensitive information such as emails, social security numbers, and bank accounts.
Factors affecting website load time on different devices and browsers can vary significantly. Users access websites through various browsers like Google Chrome, Mozilla Firefox, Safari, and Internet Explorer, each with its unique characteristics and capabilities. Additionally, the devices used to access websites, such as desktop computers, laptops, tablets, and smartphones, also impact load times.
To optimize load times across different browsers and devices, cybersecurity professionals and website developers must consider several strategies. Firstly, optimizing images and multimedia content is crucial. Compressing images and using modern image formats like WebP or JPEG 2000 can significantly reduce file sizes without compromising image quality. Similarly, using efficient video codecs and minimizing the number of videos can help decrease load times.
Another strategy is to utilize browser caching effectively. Caching allows browsers to store certain resources locally, so they do not need to be reloaded for subsequent visits. By setting appropriate cache headers and utilizing caching techniques like HTTP caching, developers can reduce the number of requests made to the server, thereby improving load times.
Furthermore, minimizing the use of external resources and third-party scripts can enhance load times across different browsers. Each external resource or script adds an additional HTTP request, potentially slowing down the website. By reducing the number of external dependencies and optimizing the ones that are necessary, developers can improve website performance.
Browser-specific code optimizations are also critical for load time optimization. Different browsers have different rendering engines and support various web technologies. By understanding these differences and optimizing code accordingly, developers can ensure smooth rendering and faster load times across multiple browsers.
In conclusion, optimizing website load times on different devices and browsers is crucial for safeguarding sensitive information and providing a seamless user experience. By considering factors such as image and multimedia optimization, effective caching, minimizing external resources, and browser-specific code optimizations, cybersecurity professionals and developers can achieve fast and secure web performance, meeting the expectations of users in terms of speed and network security.
Leveraging browser caching for improved load time
In today’s fast-paced digital world, website load time plays a crucial role in determining user experience and overall success. Slow-loading websites not only frustrate users, but they can also negatively impact search engine rankings and conversion rates. To ensure fast and secure web performance, it is essential to understand the factors that affect website load time on different devices and browsers.
One effective technique to optimize website load time is leveraging browser caching. Caching refers to the process of storing frequently accessed data, such as images, scripts, and stylesheets, on the user’s device. By caching these resources, subsequent page visits can be significantly faster, as the browser doesn’t need to request them from the server again.
Implementing browser caching involves adding HTTP headers to the server’s response, instructing the browser on how long it should cache specific resources. By setting an appropriate caching duration, you can strike a balance between reducing server requests and ensuring that users receive the most up-to-date content.
However, it’s important to consider the potential security implications of caching sensitive data. For instance, if your website deals with cybersecurity, emails, social security numbers, or bank accounts, caching such information could pose a significant risk. In such cases, it’s recommended to implement security measures, such as using secure protocols (HTTPS) and adding cache control directives to prevent caching of sensitive data.
Furthermore, different devices and browsers may have varying caching capabilities and behaviors. For instance, mobile devices often have limited storage, so caching strategies should consider the available space and prioritize essential resources. Additionally, some browsers may have aggressive caching policies, while others may ignore caching instructions altogether. It is crucial to thoroughly test your website on different devices and browsers to ensure caching is appropriately implemented and consistent across platforms.
To further enhance website load time, it is essential to consider other factors that affect performance, such as minimizing HTTP requests, optimizing images and code, and utilizing content delivery networks (CDNs). By adopting a holistic approach to web performance optimization, you can create a fast and secure browsing experience for your users while maintaining network security.
In conclusion, leveraging browser caching is a valuable technique for improving website load time. By caching frequently accessed resources, you can reduce server requests and provide a faster browsing experience for your users. However, it is crucial to balance caching with security considerations, particularly when dealing with sensitive data. Additionally, understanding the caching capabilities and behaviors of different devices and browsers is essential to ensure consistent performance across platforms. By addressing these factors and adopting a comprehensive web performance optimization strategy, you can enhance load time, network security, and overall user satisfaction.
Minifying and compressing resources to reduce load time
In today’s fast-paced digital world, website load time plays a crucial role in determining the success of online businesses. Users have become increasingly impatient, expecting websites to load within a matter of seconds. Slow loading websites not only frustrate users but also negatively impact search engine rankings. Therefore, it is essential to optimize website performance to ensure a fast and seamless user experience. One effective technique to achieve this is by minifying and compressing resources.
Minifying refers to the process of removing unnecessary characters from source code without altering its functionality. This technique helps to reduce the size of HTML, CSS, and JavaScript files, making them load faster. By eliminating comments, white spaces, and redundant code, minifying ensures that the browser can quickly parse and render the webpage.
Compression, on the other hand, involves reducing the file size by removing redundant data. Gzip compression, the most commonly used method, compresses files before they are sent over the network. This significantly reduces the file size, resulting in faster load times. Compressed files are then decompressed by the browser, ensuring that the website’s functionality remains intact.
Implementing minification and compression techniques requires careful consideration of factors that affect website load time on different devices and browsers. Websites should be optimized for various screen sizes and resolutions, ensuring a consistent user experience across devices. Additionally, different browsers may interpret and render code differently, so it’s essential to test and optimize for multiple browsers.
However, while minification and compression techniques enhance website performance, they can also introduce potential security vulnerabilities. It is crucial to ensure that the minified and compressed code is thoroughly tested for any security loopholes. Cybersecurity measures, such as firewall protection, secure passwords, and scanning, should be in place to safeguard against network security attacks.
In conclusion, minifying and compressing resources are effective techniques for reducing website load time. By optimizing HTML, CSS, and JavaScript files, website owners can significantly enhance user experience and boost search engine rankings. However, it is vital to consider the factors that affect load time on different devices and browsers. Additionally, implementing robust security measures is essential to protect against network security threats. By adopting these best practices, website owners can ensure fast and secure web performance, ultimately leading to increased user satisfaction and business success.
Chapter 4: Introduction to Network Security

Understanding the significance of network security in web performance
In today’s digital age, where cyber threats are becoming increasingly sophisticated, network security has emerged as a critical aspect of web performance. With the constant exchange of sensitive information, such as personal data, financial transactions, and confidential emails, it is imperative for organizations and individuals to prioritize network security to ensure a fast and secure web experience.
Network security encompasses a range of measures aimed at protecting networks and the data transmitted over them from unauthorized access, misuse, or modification. It plays a vital role in maintaining the trust of users and safeguarding their valuable information. This subchapter delves into the importance of network security in optimizing web performance and mitigating potential risks.
One of the key reasons network security is paramount is to safeguard against cyber threats that can compromise the confidentiality, integrity, and availability of data. Cybersecurity techniques, such as firewalls, scanning and monitoring, and secure passwords, are crucial in preventing unauthorized access to sensitive information. By implementing robust network security measures, organizations can protect their users’ emails, social security numbers, bank accounts, and other personal data from falling into the wrong hands.
Moreover, network security is directly linked to website load time and overall performance. Factors affecting website load time on different devices and browsers, such as network latency, bandwidth limitations, and content optimization, can impact user experience. Implementing effective network security measures ensures that these factors are addressed, resulting in faster load times and improved website performance.
However, network protection attacks pose a significant challenge to web performance. These attacks, such as Distributed Denial of Service (DDoS) attacks, can overwhelm servers, causing websites to slow down or become completely inaccessible. By implementing network security measures, such as firewalls and intrusion detection systems, organizations can mitigate the impact of these attacks, ensuring uninterrupted web performance.
In conclusion, network security plays a vital role in optimizing web performance and protecting sensitive information. By understanding the factors affecting website load time on different devices and browsers and implementing robust network security measures, organizations can ensure a fast and secure web experience for their users. From safeguarding emails and social security numbers to protecting bank accounts and implementing firewalls, network security is an essential aspect of maintaining website safety and security.
Cybersecurity threats and their impact on network performance
Cybersecurity threats pose a significant risk to network performance, and understanding their impact is crucial in maintaining a fast and secure web experience. This subchapter delves into the various types of cybersecurity threats that can hamper network performance, the potential consequences they can have, and the strategies to mitigate these risks.
In today’s digital landscape, cyber threats come in various forms, including malware, ransomware, phishing attacks, and Distributed Denial of Service (DDoS) attacks. These threats can infiltrate networks, compromise sensitive data such as emails, social security numbers, and bank accounts, and disrupt network operations. As organizations increasingly rely on the internet for their day-to-day operations, the impact of such threats on network performance can be severe.
One of the critical factors affecting website load time on different devices and browsers is the presence of malware or malicious code. When a website is infected, it can significantly slow down its performance, leading to frustrated users and potential loss of business. Moreover, compromised websites can also serve as a platform for spreading malware to visitors, further exacerbating the cybersecurity threat landscape.
To safeguard against these threats, organizations must implement robust network protection measures. This includes deploying firewalls to filter out suspicious traffic and implementing secure password policies to prevent unauthorized access. Regular scanning and monitoring of networks for vulnerabilities and prompt patching of any identified weaknesses are also vital in maintaining network security.
In addition, website security should not be overlooked. Implementing secure protocols such as HTTPS and ensuring the use of SSL certificates can protect data transmission between websites and users. Regular security audits and penetration testing can help identify vulnerabilities and ensure that appropriate security measures are in place.
By prioritizing network security and implementing stringent cybersecurity measures, organizations can minimize the impact of threats on network performance. This not only ensures the safety and security of sensitive data but also provides users with a fast and reliable web experience. As cyber threats continue to evolve, staying informed about the latest security trends and best practices is essential to safeguarding network performance in an ever-changing digital landscape.
Chapter 5: Network Protection Attacks and Countermeasures

Common network protection attacks and their impact on web performance
Common network protection attacks can have a significant impact on web performance, compromising the security of sensitive data such as emails, social security numbers, and bank accounts. In this subchapter, we will explore these attacks and their potential consequences, as well as discuss strategies to mitigate them.
One of the most prevalent network protection attacks is a Distributed Denial of Service (DDoS) attack. These attacks overwhelm a website or network with a massive influx of traffic, rendering it inaccessible to legitimate users. The impact on web performance is severe, as the website becomes slow or completely unresponsive. Cybercriminals often use botnets, networks of compromised computers, to launch DDoS attacks, making them difficult to trace and mitigate.
Another common attack is SQL injection. In this attack, cybercriminals exploit vulnerabilities in a website’s database by injecting malicious SQL code. This can lead to unauthorized access to sensitive information, manipulation of data, or even complete database compromise. The impact on web performance can be seen in slow load times and frequent server errors.
Cross-Site Scripting (XSS) attacks involve injecting malicious scripts into web pages viewed by users. These scripts can then be executed by their browsers, allowing cybercriminals to steal sensitive information or manipulate website content. XSS attacks not only compromise the security of user data but can also impact web performance by causing browser crashes or slowing down page rendering.
Phishing attacks are another prevalent network protection threat. Cybercriminals impersonate legitimate websites or send deceptive emails to trick users into revealing their login credentials or other sensitive information. The impact on web performance may not be immediate, but the loss of user trust and potential reputation damage can have long-term consequences for a website’s success.
To protect against these attacks, implementing a strong network security infrastructure is crucial. This includes firewalls, secure passwords, regular scanning and monitoring for vulnerabilities, and keeping software up to date. Additionally, website owners should prioritize the need for speed by optimizing website load times on different devices and browsers. This can be achieved through techniques such as caching, content delivery networks, and minimizing resource requests.
In conclusion, network protection attacks pose a significant threat to web performance and the security of sensitive data. By understanding these attacks and implementing robust security measures, website owners can ensure fast and secure web performance, safeguarding their users’ information and maintaining their reputation.
Denial of Service (DoS) attacks and their prevention
In today’s digital landscape, the threat of cyber attacks looms large, with hackers constantly finding new ways to exploit vulnerabilities in network security. One such attack is the Denial of Service (DoS) attack, which can wreak havoc on a website’s performance and compromise sensitive user data. In this subchapter, we will delve into the intricacies of DoS attacks and explore effective prevention strategies to ensure the safety and security of your network.
A DoS attack aims to overwhelm a website or online service by flooding it with an excessive amount of traffic or requests, rendering it unable to respond to legitimate users. The consequences can be severe, ranging from temporary disruption of services to complete downtime, resulting in significant financial losses, reputational damage, and compromised user trust. Cybercriminals may utilize a variety of techniques, including botnets, amplification attacks, or resource depletion attacks to initiate a DoS attack.
To effectively prevent DoS attacks, it is crucial to implement robust network protection measures. One of the first lines of defense is a powerful firewall that can detect and filter out malicious traffic. By analyzing network traffic patterns and identifying abnormal behavior, firewalls can mitigate the impact of DoS attacks and prevent unauthorized access to sensitive data.
Additionally, proactive scanning and monitoring of network traffic can help identify and thwart potential DoS attacks before they cause any harm. Regularly monitoring network traffic and keeping an eye out for unusual spikes in traffic can enable early detection and swift response to mitigate the impact of an attack.
Another critical aspect of DoS attack prevention is ensuring the security of your website itself. Implementing secure password policies, encrypting sensitive data, and regularly updating software and applications can significantly reduce the risk of exploitation. Employing a comprehensive website security solution that includes vulnerability scanning, malware detection, and intrusion prevention can further enhance your network’s resilience against DoS attacks.
While safeguarding against DoS attacks is paramount, it is equally important to strike a balance between security and website load time. Factors such as device compatibility and browser optimization play a significant role in determining the load time of a website. By considering these factors and implementing best practices for optimizing website performance, you can deliver a fast and secure browsing experience to your users.
In conclusion, DoS attacks pose a significant threat to network security and the integrity of sensitive user data. By implementing robust network protection measures, regularly monitoring network traffic, and ensuring website security, you can effectively prevent DoS attacks and safeguard your organization’s assets and reputation.
Distributed Denial of Service (DDoS) attacks and mitigation techniques
In today’s interconnected world, where businesses heavily rely on their online presence, ensuring network security has become more critical than ever. One of the most pervasive threats faced by organizations is the Distributed Denial of Service (DDoS) attack. This subchapter will delve into the intricacies of DDoS attacks, their potential impact, and effective mitigation techniques.
A DDoS attack occurs when a multitude of compromised systems flood a targeted website or network with an overwhelming amount of traffic, rendering it inaccessible to legitimate users. These attacks can result in substantial financial losses, reputational damage, and customer dissatisfaction. It is therefore essential for cybersecurity professionals to understand the various types of DDoS attacks and develop appropriate strategies to mitigate them.
There are several types of DDoS attacks, including volumetric attacks, which overload the network with a massive amount of traffic, and application layer attacks, which exploit vulnerabilities in specific applications or services. Understanding the attacker’s motives and techniques is crucial in implementing effective mitigation measures.
To combat DDoS attacks, organizations must adopt a multi-layered approach that combines robust network infrastructure, vigilant monitoring, and proactive incident response. This includes implementing firewalls, intrusion detection systems, and load balancers to filter out malicious traffic and ensure optimal network performance. Additionally, organizations should establish incident response plans to minimize the impact of an attack and swiftly restore normal operations.
In recent years, advanced mitigation techniques have emerged to counter increasingly sophisticated DDoS attacks. These techniques include rate limiting, which restricts the amount of traffic allowed from a single source, and traffic engineering, which reroutes traffic to absorb the attack. Employing these mitigation techniques can significantly reduce the impact of DDoS attacks and maintain network availability.
To enhance network security, organizations must also prioritize regular scanning and monitoring of their systems for vulnerabilities. Implementing secure passwords and regularly updating software and firmware are essential steps in preventing potential entry points for attackers. Additionally, employing website security measures such as SSL certificates and encryption can safeguard sensitive user information, such as social security numbers and bank accounts.
In conclusion, DDoS attacks pose a significant threat to network security and can have severe consequences for businesses. By understanding the various types of DDoS attacks and implementing effective mitigation techniques, cybersecurity professionals can ensure the safety and security of their organizations. By adopting a multi-layered approach, organizations can protect their networks, mitigate the impact of attacks, and provide a fast and secure web performance for their users.
Chapter 6: Scanning and Monitoring for Network Security

Importance of proactive scanning and monitoring for network security
In today’s digital age, where cyber threats are becoming increasingly sophisticated, it is crucial for organizations to prioritize network security. The ever-evolving landscape of cybersecurity demands a proactive approach to scanning and monitoring to ensure the safety and security of sensitive data, such as emails, social security numbers, and bank accounts.
One of the fundamental aspects of network security is the implementation of a robust firewall. While a firewall acts as a barrier between a trusted internal network and an untrusted external network, it is only effective if it is regularly scanned and monitored. Proactive scanning helps identify any vulnerabilities or misconfigurations that could be exploited by cybercriminals. By continuously monitoring the firewall, organizations can quickly detect and respond to any suspicious activities or unauthorized access attempts, safeguarding the network from potential threats.
The need for speed in today’s digital world is undeniable. However, it should not come at the expense of network protection. Cybercriminals are constantly devising new methods to exploit vulnerabilities, and organizations need to be one step ahead. Proactive scanning and monitoring play a vital role in identifying and mitigating potential security breaches, ensuring that network performance and security go hand in hand.
Network security attacks can have devastating consequences for both individuals and organizations. From financial loss to reputational damage, the impact can be far-reaching. Proactive scanning and monitoring provide organizations with real-time visibility into their network, enabling them to detect and respond to potential threats promptly. By identifying and addressing vulnerabilities before they are exploited, organizations can minimize the risk of a security breach and protect their valuable assets.
A key aspect of network security is ensuring secure passwords are implemented throughout the organization. Proactive scanning and monitoring can help identify weak or compromised passwords and enforce stronger password policies, reducing the risk of unauthorized access. Additionally, regular scanning can detect any unauthorized devices or connections on the network, preventing potential breaches and ensuring that only authorized users have access to sensitive information.
In conclusion, proactive scanning and monitoring are essential components of network security. By continuously assessing vulnerabilities, monitoring network activity, and ensuring secure passwords, organizations can stay ahead of cyber threats and protect their valuable data. In the face of ever-evolving cyber risks, proactive scanning and monitoring are crucial for maintaining a secure network environment.
Vulnerability scanning and its role in identifying security loopholes
In today’s digital landscape, where cybersecurity threats are becoming increasingly sophisticated, it is essential for organizations to implement robust security measures to protect their sensitive data. One such measure is vulnerability scanning, a proactive approach that helps identify security loopholes within a network or system before they can be exploited by malicious actors.
Vulnerability scanning involves the use of specialized software tools to scan an organization’s network, system, or application for potential vulnerabilities. These vulnerabilities can range from outdated software versions and misconfigurations to weak passwords and unpatched vulnerabilities. By conducting regular vulnerability scans, organizations can stay one step ahead of potential threats and take prompt action to mitigate any identified vulnerabilities.
The role of vulnerability scanning in identifying security loopholes cannot be overstated. It serves as a crucial component of a robust cybersecurity strategy, enabling organizations to identify and assess potential risks and weaknesses within their network infrastructure. By conducting regular vulnerability scans, organizations can gain valuable insights into their security posture and take appropriate measures to address any identified vulnerabilities.
One of the key benefits of vulnerability scanning is its ability to provide organizations with a comprehensive view of their cybersecurity landscape. By scanning network devices, servers, and applications, organizations can identify potential entry points for attackers and prioritize their security efforts accordingly. This helps organizations allocate resources effectively and implement targeted security measures to protect critical assets such as emails, social security numbers, and bank accounts.
Furthermore, vulnerability scanning plays a vital role in ensuring compliance with industry regulations and standards. Many regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA), require organizations to regularly conduct vulnerability scans to identify and address potential security vulnerabilities.
In conclusion, vulnerability scanning is a crucial component of any comprehensive cybersecurity strategy. By regularly scanning their network and systems, organizations can proactively identify and address security loopholes, reducing the risk of data breaches and other cybersecurity incidents. With the ever-evolving threat landscape, organizations must prioritize vulnerability scanning to safeguard their sensitive information and maintain a strong security posture.
Intrusion detection and prevention systems for network security
In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, protecting sensitive data is paramount. One of the key components of a robust network security strategy is the implementation of intrusion detection and prevention systems (IDPS). This subchapter aims to provide an in-depth understanding of IDPS and their crucial role in safeguarding networks from unauthorized access, attacks, and potential data breaches.
An intrusion detection system (IDS) is designed to monitor network traffic and identify any suspicious or malicious activity. This can include unauthorized attempts to access a network, abnormal traffic patterns, or the presence of known malware signatures. By analyzing network packets and comparing them against a predefined set of rules, an IDS can detect potential threats and generate alerts for further investigation.
On the other hand, an intrusion prevention system (IPS) not only detects potential threats but also takes immediate action to prevent them from compromising the network. This can involve blocking specific IP addresses, terminating suspicious connections, or applying security patches or updates in real-time. By proactively mitigating threats, an IPS acts as a critical line of defense against attacks.
In combination, IDS and IPS provide comprehensive network security by detecting, preventing, and responding to potential threats in real-time. They form an integral part of a layered security approach, working alongside firewalls, secure passwords, and other security measures to create a robust defense system.
The importance of IDPS becomes even more apparent when considering the types of sensitive data that organizations need to protect. Cybersecurity breaches can result in the compromise of personal information such as social security numbers, bank accounts, or confidential emails. The financial and reputational damage caused by such breaches can be significant, making it imperative for organizations to invest in effective network security solutions.
Scanning and monitoring are crucial aspects of IDPS, ensuring that network traffic is constantly analyzed for potential threats. Regular vulnerability assessments and penetration testing help identify weaknesses in the network infrastructure and enable proactive measures to address them. Additionally, continuous monitoring allows security teams to quickly detect and respond to any unusual activity, minimizing the potential impact of an attack.
In conclusion, IDPS play a vital role in ensuring network security in today’s digital landscape. With the increasing complexity and frequency of cyber threats, organizations must invest in robust and effective security measures to protect their sensitive data. By implementing intrusion detection and prevention systems, organizations can enhance their network security posture, safeguarding critical information and maintaining the trust and confidence of their customers.
Chapter 7: Ensuring Web Security

Secure password management and its impact on web performance
Secure password management is crucial for maintaining the safety and security of our online accounts. In today’s digital age, where cyber threats are becoming increasingly sophisticated, it is more important than ever to employ strong password practices. Not only does secure password management protect our personal information, such as emails, social security numbers, and bank accounts, but it also plays a significant role in web performance.
When it comes to web performance, every second counts. Users expect websites to load quickly and efficiently, and any delays can lead to frustration and abandonment. One of the factors that can impact website load time is the authentication process, which involves users entering their passwords to access their accounts. If the password management system is not secure, it can slow down the process and affect the overall performance.
A secure password management system ensures that passwords are stored in an encrypted format, making it difficult for hackers to decipher them. This encryption adds an extra layer of protection to user accounts and prevents unauthorized access. Moreover, secure password management systems often include features such as password strength checks and two-factor authentication, further enhancing the security of user accounts.
From a web performance perspective, secure password management systems improve efficiency by streamlining the authentication process. When users enter their passwords, the system can quickly verify their credentials and grant access to their accounts. This reduces the time it takes to authenticate users and enhances the overall user experience.
Additionally, secure password management systems can also prevent brute force attacks, where hackers attempt to gain access to user accounts by systematically trying numerous password combinations. These attacks can significantly impact web performance as they consume server resources and slow down the authentication process. With a secure password management system in place, such attacks can be mitigated, ensuring a smooth and uninterrupted web experience for users.
In conclusion, secure password management is not only essential for protecting our online accounts but also plays a vital role in web performance. By implementing secure password practices and utilizing robust password management systems, we can enhance the security of our accounts while ensuring fast and efficient web performance.
Best practices for creating and managing secure passwords
In today’s digital age, where cyber threats are on the rise, it has become crucial for individuals and organizations to prioritize the security of their online accounts and sensitive information. One of the fundamental aspects of online security is the creation and management of secure passwords. This subchapter will provide you with best practices for creating and managing strong passwords to help safeguard your personal data and mitigate the risk of unauthorized access.
When it comes to creating a secure password, complexity is key. A strong password should be at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information such as birthdates, names, or common words. Instead, opt for random combinations that are difficult to crack.
It is essential to use unique passwords for each of your online accounts. Reusing passwords across multiple platforms increases the vulnerability of your accounts. If one account gets breached, all your other accounts will be at risk as well. To manage multiple passwords effectively, consider using a password manager tool. These tools generate and store strong passwords for you, eliminating the need to remember them all.
Regularly updating your passwords is another crucial practice. Set a reminder to change your passwords every three to six months to ensure maximum security. Additionally, be cautious of phishing attempts and never share your passwords with anyone. Legitimate organizations will never ask for your password over email or phone.
In addition to following these best practices for password creation, it is equally important to implement strong security measures on your devices and networks. Utilize firewalls and keep your antivirus software up to date to protect against malware and other threats. Regularly scan your devices and network for vulnerabilities and monitor for any suspicious activities.
By implementing these best practices for creating and managing secure passwords, you are taking a proactive approach towards safeguarding your personal and sensitive information. Remember, your online security is in your hands, and by following these guidelines, you can significantly reduce the risk of falling victim to cyber-attacks and ensure a safe and secure online experience.
Importance of website security for overall network protection
In today’s digital age, ensuring the security of websites is of utmost importance. As cyber threats continue to evolve and become more sophisticated, it is crucial for organizations to prioritize website security as an essential component of overall network protection. This subchapter explores the significance of website security and its impact on safeguarding sensitive information, such as cybersecurity, cybersecurity technique strategy, emails, social security numbers, bank accounts, and more.
One of the primary reasons why website security is vital is the prevalence of cyber attacks that target users’ personal and financial data. Hackers constantly exploit vulnerabilities in websites to gain unauthorized access to sensitive information, which can have severe consequences for individuals and organizations alike. By implementing robust website security measures, such as firewalls, secure passwords, and scanning and monitoring tools, businesses can significantly reduce the risk of data breaches and protect their customers’ privacy.
Moreover, a secure website not only safeguards user data but also enhances the overall trust and credibility of the organization. Internet users are becoming increasingly cautious about sharing their personal information online due to the rising number of cyber threats. Therefore, by demonstrating a commitment to website security, businesses can establish a positive reputation and attract more customers.
Additionally, website security plays a crucial role in mitigating the impact of network protection attacks. Many cyber attacks, such as Distributed Denial of Service (DDoS) attacks, target websites to disrupt their availability and functionality. By implementing adequate security measures, organizations can effectively counter such attacks and ensure uninterrupted access to their websites, thus minimizing potential financial losses and reputational damage.
Furthermore, factors affecting website load time on different devices and browsers are closely linked to website security. Slow-loading websites not only result in a poor user experience but also provide opportunities for attackers to exploit vulnerabilities. By addressing these factors, such as optimizing website code, leveraging caching techniques, and utilizing content delivery networks, organizations can improve both website performance and security.
In conclusion, website security is essential for overall network protection. By prioritizing website security, organizations can safeguard sensitive information, enhance trust and credibility, mitigate network protection attacks, and optimize website load time. In an era dominated by cyber threats, investing in website security is not only a business imperative but also a responsibility towards ensuring the privacy and safety of users’ online interactions.
SSL/TLS encryption and its role in website security
In today’s digital age, where online threats are becoming increasingly sophisticated, ensuring the security of websites has become a top priority for organizations. One of the key components of website security is SSL/TLS encryption, which plays a critical role in protecting sensitive data and establishing trust between websites and their users.
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that encrypt data transmitted between a user’s browser and a web server. This encryption ensures that the data cannot be intercepted or tampered with by unauthorized parties. By implementing SSL/TLS encryption, website owners can safeguard sensitive information such as passwords, credit card details, and personal identification information from potential attackers.
The role of SSL/TLS encryption in website security is multi-faceted. Firstly, it provides data confidentiality by encrypting the information exchanged between a user and a website. This means that even if an attacker manages to intercept the data, they won’t be able to decipher its contents without the encryption key.
Secondly, SSL/TLS encryption establishes the authenticity of a website. When a website has an SSL/TLS certificate installed, it enables the use of HTTPS (Hypertext Transfer Protocol Secure) instead of the standard HTTP. This indicates to users that the website has undergone a verification process and that their connection is secure. Users are more likely to trust websites with SSL/TLS encryption, leading to increased customer confidence and loyalty.
Furthermore, SSL/TLS encryption helps protect against phishing attacks. Phishing is a technique used by cybercriminals to trick users into providing their sensitive information by impersonating legitimate websites. With SSL/TLS encryption, users can visually verify the website’s authenticity through the presence of a padlock icon or a green address bar, providing an additional layer of protection against phishing attempts.
In conclusion, SSL/TLS encryption is a crucial component of website security. It not only encrypts sensitive data but also establishes trust between websites and their users. By implementing SSL/TLS encryption, organizations can protect against data breaches, bolster customer trust, and mitigate the risk of phishing attacks. In today’s digital landscape, where cybersecurity threats are ever-present, SSL/TLS encryption is an essential tool for ensuring fast and secure web performance.
Chapter 8: Firewall and Network Security

Understanding the role of firewalls in network security
In today’s digital age, network security has become a paramount concern for individuals and organizations alike. With the increasing number of cybersecurity threats targeting sensitive information such as emails, social security numbers, and bank accounts, it is crucial to establish robust measures to protect against potential breaches. One such measure that plays a pivotal role in network security is the firewall.
A firewall acts as a barrier between an internal network and the external world, filtering incoming and outgoing network traffic based on predetermined security rules. Its primary objective is to prevent unauthorized access to the network while allowing legitimate traffic to pass through. By monitoring and controlling network traffic, firewalls act as the first line of defense against malicious activities, ensuring the safety and security of the network.
Firewalls serve as a critical component in safeguarding against various network protection attacks, including unauthorized access attempts, malware infections, and data exfiltration. They achieve this by employing several techniques such as packet filtering, application filtering, and stateful inspection. Packet filtering examines individual packets of data based on predefined rules, allowing or denying their passage. Application filtering, on the other hand, examines the content of the data packets to determine if they comply with the protocols and applications being used. Stateful inspection maintains context awareness by examining the state of the connection and allowing only legitimate traffic to pass through.
In addition to their security-enhancing capabilities, firewalls also facilitate scanning and monitoring of network traffic. They can detect and block suspicious activities, alert administrators about potential threats, and log network events for further analysis. This proactive approach allows network administrators to identify and mitigate security risks promptly.
To ensure the effectiveness of firewalls, it is crucial to implement secure password practices, regularly update firewall firmware, and configure them according to the specific network requirements. Additionally, integrating firewalls with other security measures such as intrusion detection systems and antivirus software enhances the overall network security posture.
In conclusion, firewalls play a crucial role in network security by acting as a barrier against unauthorized access and malicious activities. They provide protection against a wide range of network protection attacks, while also facilitating scanning, monitoring, and logging of network traffic. By understanding the role of firewalls and implementing them effectively, organizations can enhance their network security and safeguard sensitive information from potential threats.
Types of firewalls and their effectiveness in protecting networks
In today’s digital age, where cybersecurity threats are becoming increasingly sophisticated, it is crucial for businesses and individuals to prioritize network security. Firewalls play a vital role in safeguarding networks from malicious attacks and unauthorized access. In this subchapter, we will explore the different types of firewalls and their effectiveness in protecting networks.
- Packet Filtering Firewalls: This type of firewall examines each packet of data that passes through the network, based on predetermined rules. It filters packets based on source and destination IP addresses, ports, and protocols. While packet filtering firewalls are quick and efficient, they lack the ability to inspect the contents of the packets, leaving them vulnerable to more advanced attacks.
- Stateful Inspection Firewalls: These firewalls not only analyze individual packets but also keep track of the connection state. They maintain a record of the entire conversation between two hosts, allowing them to identify and block suspicious traffic. Stateful inspection firewalls offer improved security compared to packet filtering firewalls, but they may still struggle with detecting more sophisticated threats.
- Application-Level Gateways (Proxy Firewalls): Proxy firewalls act as intermediaries between the client and the server, inspecting each packet at the application layer. They offer the highest level of security as they can analyze the content of the traffic and make informed decisions. However, the drawback of proxy firewalls is that they can introduce latency due to the additional processing required.
- Next-Generation Firewalls (NGFW): NGFWs combine traditional firewall functionality with additional security features like intrusion prevention, deep packet inspection, and antivirus filtering. They are designed to combat advanced threats, including malware and ransomware. NGFWs provide enhanced protection but may require more resources and configuration expertise.
- Unified Threat Management (UTM) Firewalls: UTM firewalls integrate multiple security features into a single device, including firewall, antivirus, intrusion detection, virtual private network (VPN), and web filtering. They offer a comprehensive approach to network security, particularly for small to medium-sized businesses. However, UTM firewalls may face performance limitations when handling heavy network traffic.
While each type of firewall has its strengths and weaknesses, the effectiveness of a firewall ultimately depends on its configuration and the expertise of the network administrators. Employing a combination of different firewall technologies, along with regular updates and patches, can significantly enhance network security.
In conclusion, selecting the right type of firewall and configuring it properly is crucial for protecting networks against cyber threats. Organizations must evaluate their specific security requirements and choose a firewall solution that aligns with their needs. Remember, network security is an ongoing process that requires constant monitoring, updates, and proactive measures to stay ahead of evolving threats.
Chapter 9: Need for Speed: Balancing Load Time and Network Security
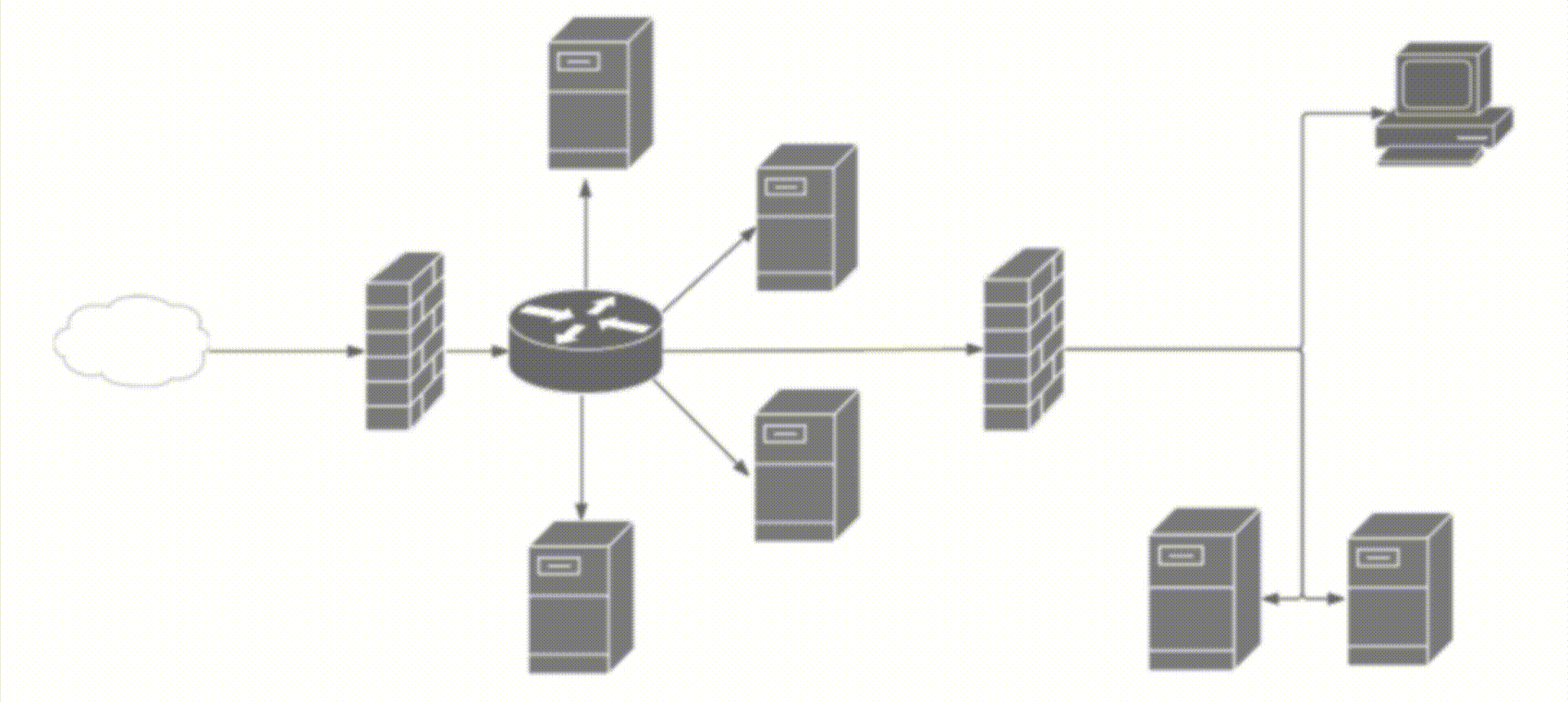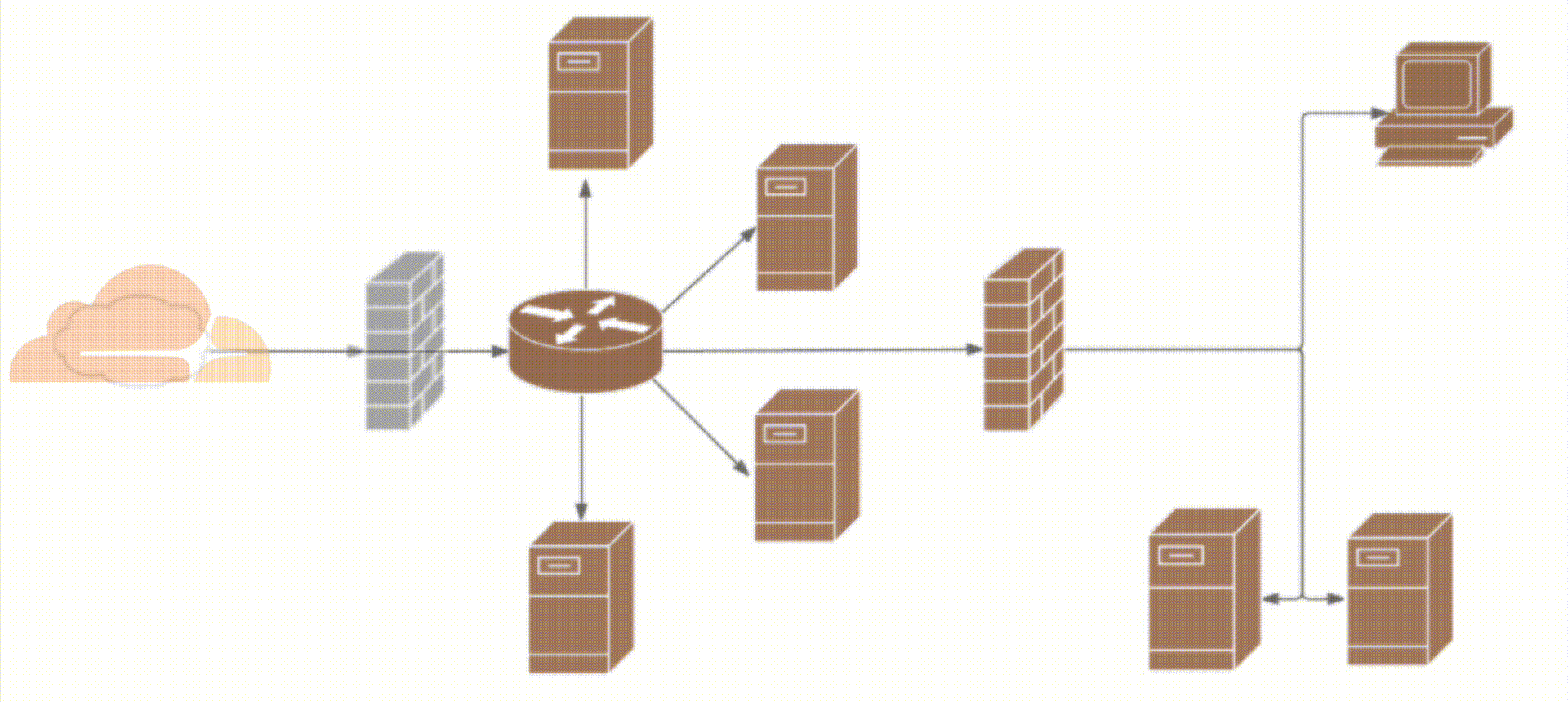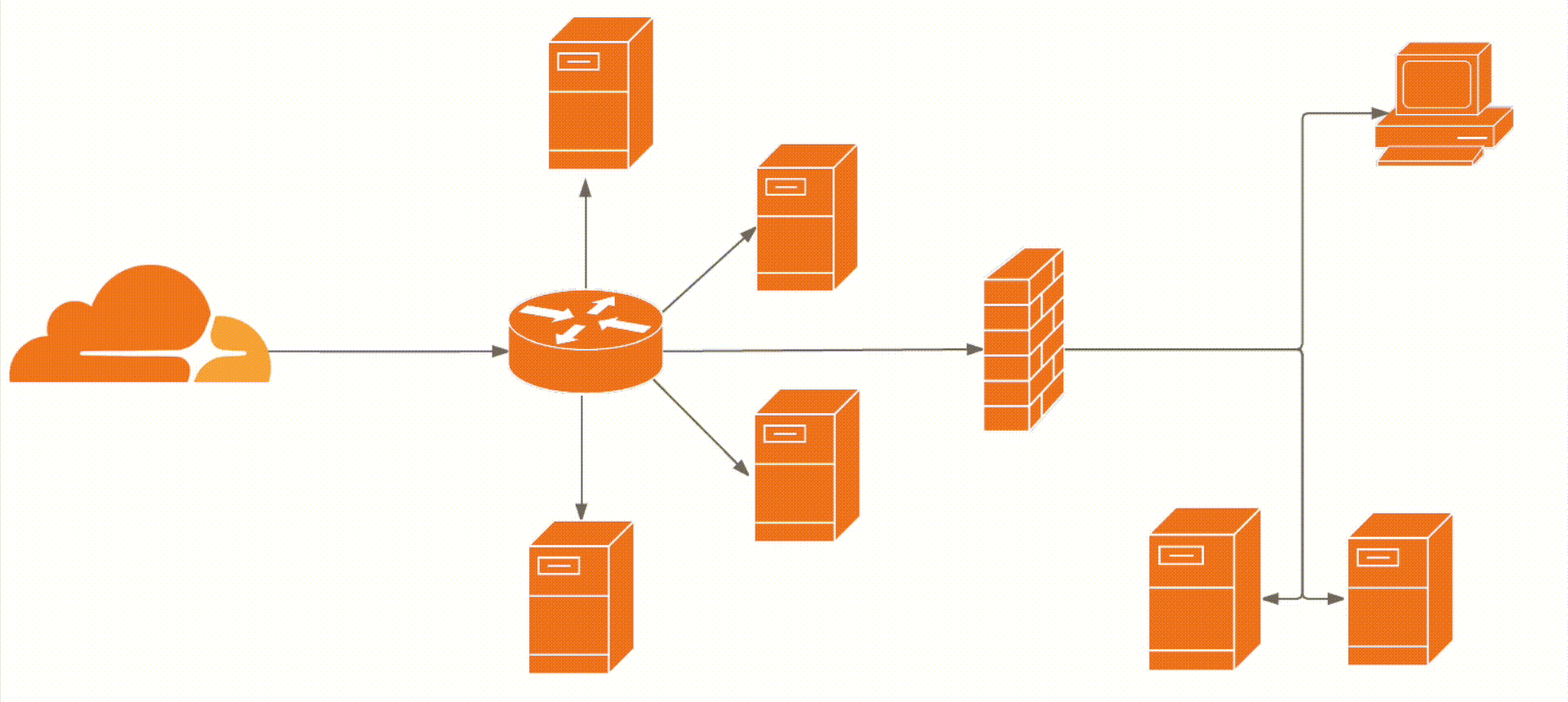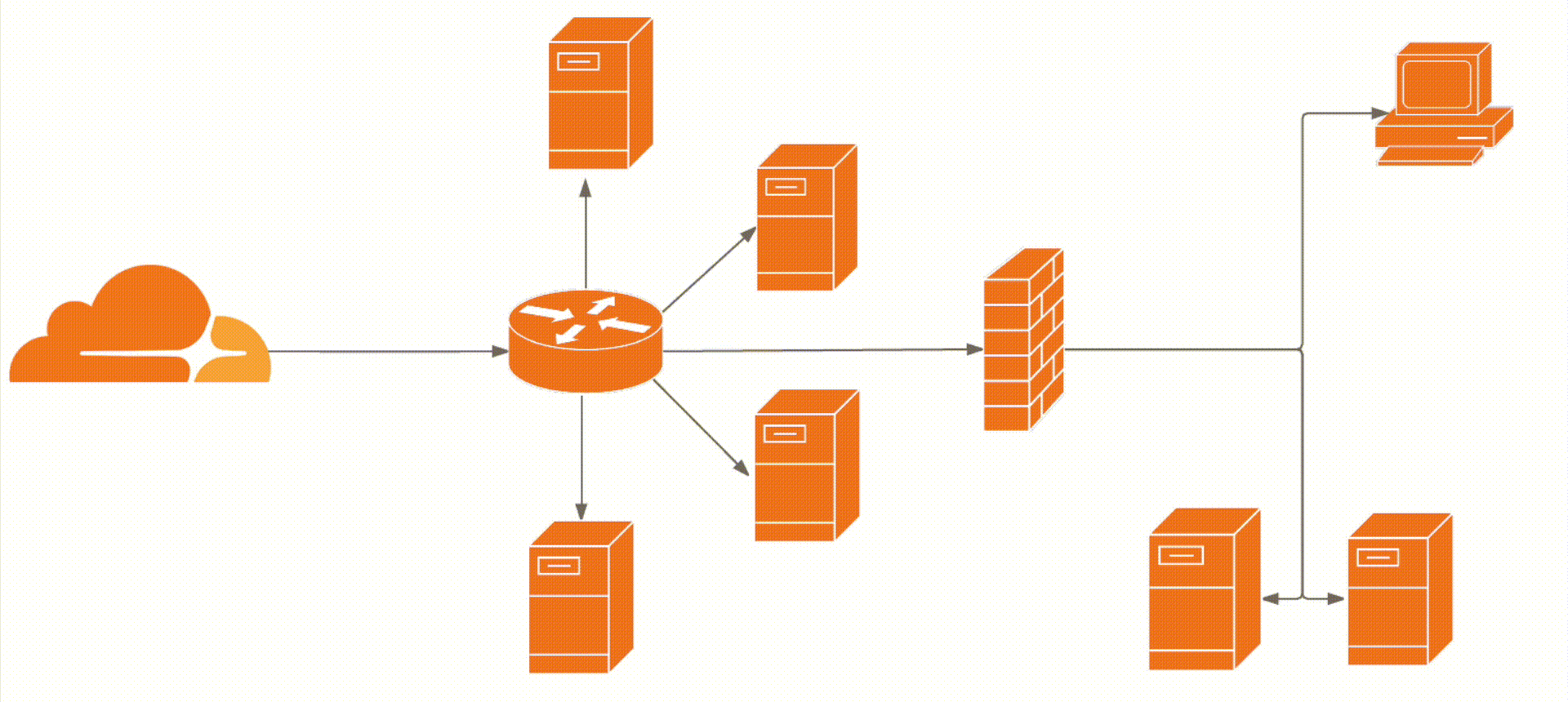
Striking the right balance between load time optimization and network security
Striking the right balance between load time optimization and network security is crucial for organizations seeking to provide a fast and secure web performance. In today’s digital landscape, where cyber threats are rampant and user expectations for faster website load times are high, finding the equilibrium between these two aspects is paramount.
Factors affecting website load time on different devices and browsers play a significant role in determining the user experience. With the rise of mobile devices, websites must be optimized to load quickly on smartphones and tablets. Slow load times can lead to frustrated users, higher bounce rates, and ultimately, loss of potential customers. It is essential to understand the technical considerations that impact load times, such as image optimization, code minification, and efficient caching mechanisms.
However, while focusing on load time optimization, organizations should not neglect network security. Cybersecurity threats, such as phishing attacks, malware injections, and data breaches, pose significant risks to user data and can severely damage an organization’s reputation. Implementing robust security measures, such as firewalls, scanning and monitoring tools, and secure passwords, is crucial to safeguard sensitive information, including email addresses, social security numbers, and bank accounts.
In this subchapter, we will explore the delicate balance between load time optimization and network security. We will delve into the best practices for ensuring fast website performance while maintaining robust security measures. By understanding the potential trade-offs between load time and security, organizations can make informed decisions to strike the right balance.
We will discuss the importance of implementing proper website security protocols to protect against network protection attacks. Additionally, we will explore the need for continuous monitoring and scanning of web applications to identify vulnerabilities and proactively address them. By adopting a proactive approach to security, organizations can minimize the risk of data breaches and mitigate potential damage.
Ultimately, finding the sweet spot between load time optimization and network security is a continuous process. It requires a comprehensive understanding of the latest technologies, security threats, and best practices. By implementing effective strategies and staying up-to-date with the evolving landscape of cybersecurity, organizations can deliver fast and secure web performance that meets user expectations while keeping their valuable data safe and secure.
Performance trade-offs in implementing security measures
In today’s digital landscape, ensuring both fast and secure web performance is of utmost importance. As cyber threats continue to evolve and become more sophisticated, implementing robust security measures is essential to protect sensitive information such as emails, social security numbers, and bank accounts. However, it is crucial to acknowledge that there are trade-offs in performance when it comes to implementing these security measures.
One of the main factors affecting website load time on different devices and browsers is the implementation of firewalls. Firewalls act as a barrier between the internal network and external sources, filtering out malicious traffic and protecting against network protection attacks. While firewalls provide an essential layer of security, they can also introduce latency and increase website load time. This is because the firewall needs to inspect incoming and outgoing traffic, which takes time and can impact overall performance.
Another factor to consider is the need for speed. Users expect websites to load quickly, and any delays can result in frustration and a negative user experience. Implementing robust security measures, such as scanning and monitoring for vulnerabilities, can help identify and prevent potential security breaches. However, these processes can also consume resources and impact website performance. Balancing the need for speed with the need for security is a delicate task that requires careful consideration.
Secure passwords are another crucial aspect of website security. Implementing strong password policies and encryption techniques can help safeguard user accounts and sensitive information. However, enforcing complex passwords and encryption algorithms can increase the time it takes for users to log in and access their accounts. Striking a balance between security and user convenience is necessary to maintain a positive user experience while ensuring robust security measures are in place.
Website security is a multifaceted challenge that requires a comprehensive approach. It is essential to consider the trade-offs in performance that come with implementing security measures. Factors such as firewalls, the need for speed, secure passwords, and other security measures all impact website load time and user experience. Finding the right balance between security and performance is crucial to ensuring a fast and secure web performance. By understanding these trade-offs and implementing appropriate measures, organizations can protect sensitive information while providing a seamless user experience.
Chapter 10: Conclusion
Recap of the importance of load time and network security in web performance
In today’s digital landscape, where the internet plays a critical role in our lives, ensuring fast and secure web performance is of utmost importance. This chapter provides a recap of the significance of load time and network security in achieving optimal web performance, with a focus on factors affecting website load time on different devices and browsers.
Load time, or the time it takes for a webpage to fully load and display its content, is a crucial aspect of web performance. In today’s fast-paced world, users expect websites to load quickly and efficiently. Slow load times not only hinder user experience but can also lead to decreased website traffic, higher bounce rates, and ultimately, loss of potential customers. It is essential for organizations to optimize their website’s load time to stay ahead of the competition and retain user engagement.
Factors affecting website load time can vary depending on the devices and browsers used by the audience. Mobile devices have become increasingly popular for browsing the internet, and optimizing websites for mobile load time is vital. Mobile-specific factors like responsive design, efficient coding, and compressed images can significantly improve load time on smartphones and tablets. Similarly, different browsers have their own performance characteristics and capabilities. Understanding these nuances and optimizing websites accordingly can ensure a seamless user experience across various browsers.
Network security is another critical aspect of web performance. With the rise in cyber threats and data breaches, safeguarding sensitive information, such as emails, social security numbers, and bank accounts, has become paramount. A robust network security strategy, including a firewall, secure passwords, scanning, monitoring, and website security measures, is necessary to protect against network protection attacks.
Network security not only safeguards user data but also contributes to improved web performance. Malicious activities, such as Distributed Denial-of-Service (DDoS) attacks, can significantly slow down websites and disrupt user experience. By implementing effective network security measures, organizations can mitigate the risk of such attacks and ensure uninterrupted website performance.
In conclusion, load time and network security are two crucial pillars of web performance. Optimizing website load time for different devices and browsers, while ensuring robust network security, is essential for organizations to provide a fast and secure online experience to their audience. By prioritizing these aspects, organizations can enhance user engagement, protect sensitive information, and maintain a competitive edge in the digital landscape.
Key takeaways for ensuring fast and secure web performance
In today’s digital age, ensuring fast and secure web performance is crucial for businesses and individuals alike. Slow-loading websites not only frustrate users but also negatively impact search engine rankings and customer trust. Additionally, an insecure website can expose sensitive information, such as social security numbers and bank accounts, to cybercriminals. To help you optimize your web performance and safeguard your data, here are some key takeaways:
1. Factors Affecting Website Load Time on Different Devices and Browsers:
- Device capabilities: Different devices have varying processing power and network connectivity, impacting load times. Optimize your website for mobile devices to cater to the increasing mobile user base.
- Browser compatibility: Different browsers interpret website code differently, affecting load times. Regularly test your website across popular browsers to ensure compatibility and optimal performance.
- Content optimization: Large files, such as images or videos, can significantly slow down load times. Compress and optimize your website’s content to reduce file sizes without compromising quality.
- CDN utilization: Content Delivery Networks (CDNs) distribute website content across geographically dispersed servers, reducing latency and improving load times. Consider leveraging CDNs to enhance web performance.
2. Network Protection Attacks and Security Measures
- Firewall implementation: A robust firewall acts as a first line of defense against network attacks. Regularly update and configure your firewall to prevent unauthorized access and potential data breaches.
- Scanning and monitoring: Regularly scan your website for vulnerabilities and potential malware. Continuous monitoring helps detect any suspicious activities and enables quick remediation.
- Secure passwords: Weak passwords are a common entry point for hackers. Encourage users to create strong passwords and implement multi-factor authentication for enhanced security.
- Website security protocols: Implement HTTPS encryption and SSL/TLS certificates to secure data transmission and protect sensitive information from interception.
3. Need for Speed and Web Performance Optimization
- Minimize HTTP requests: Reduce the number of requests made to the server by combining files, leveraging browser caching, and eliminating unnecessary scripts.
- Code optimization: Optimize your website’s code to improve efficiency and reduce load times. Remove unnecessary code, use minification techniques, and optimize database queries.
- Responsive design: Ensure your website is responsive and adaptable to different screen sizes. Responsive design enhances user experience and improves load times on various devices.
- Regular performance testing: Conduct regular performance testing to identify bottlenecks and optimize your website accordingly. Tools like Google PageSpeed Insights can provide valuable insights.
By considering these key takeaways, you can enhance your website’s load time and network security, providing a seamless and secure browsing experience for your users while protecting sensitive data from potential cyber threats. Prioritizing fast and secure web performance not only improves user satisfaction but also mitigates the risk of cyber attacks and data breaches.
Our team of developers created this web store to assist businesses in safeguarding their website contact forms from spam and abuse. Contact us to address your website contact form spam issues.
The post Load Time and Network Security: Ensuring Fast and Secure Web Performance appeared first on Stop Web Form Spam.
https://media.istockphoto.com/id/945479254/vector/loading-page-browser-in-flat-style-vector-illustration.jpg?s=612x612&w=0&k=20&c=9kbWb7oC6zwTTgXVn9dJpdtK-dQEAkj0PqQC825PFBg=
https://www.stopwebformspam.com/load-time-and-network-security-ensuring-fast-and-secure-web-performance/?utm_source=rss&utm_medium=rss&utm_campaign=load-time-and-network-security-ensuring-fast-and-secure-web-performance
Comments
Post a Comment